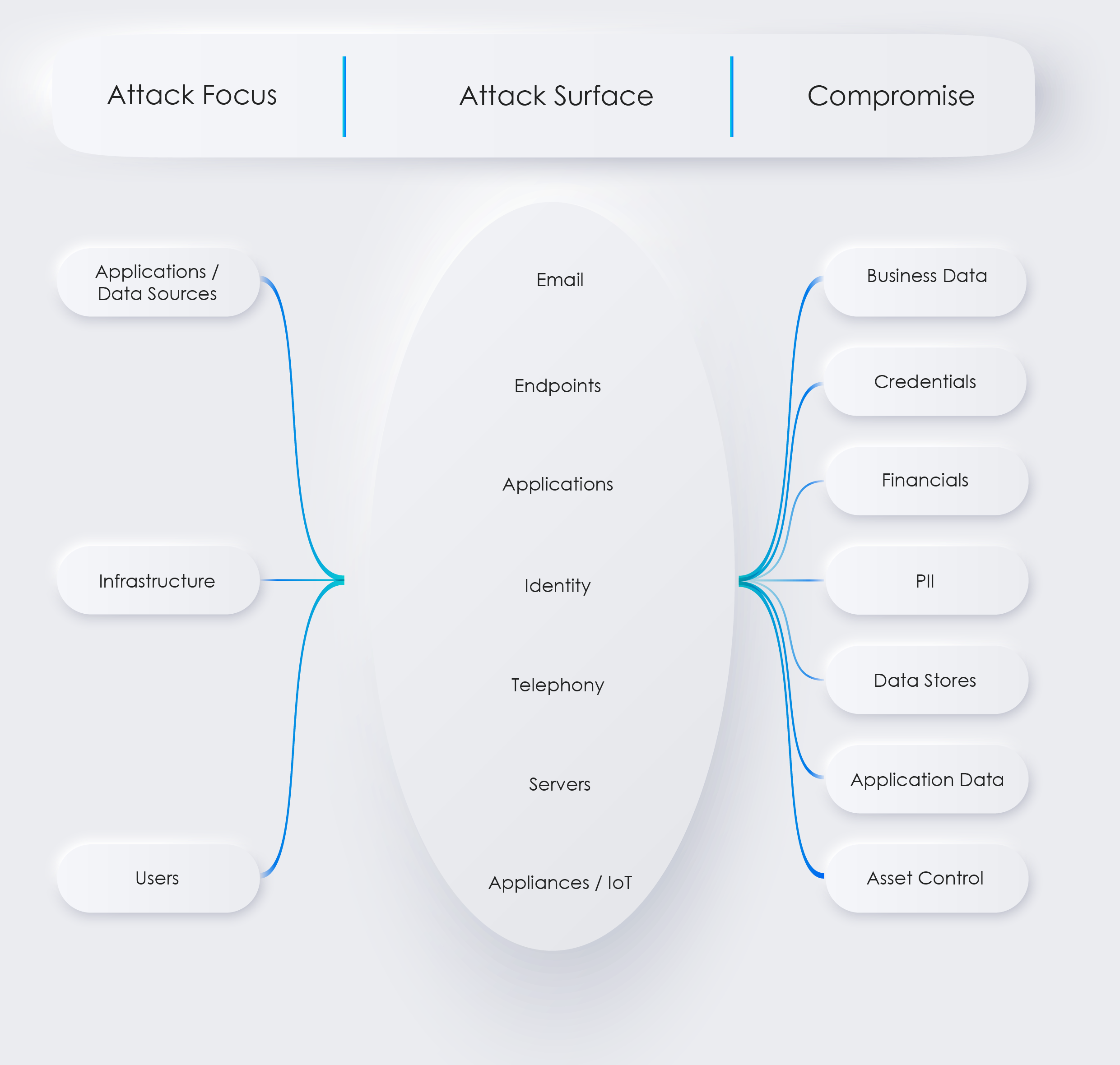
We developed our security posture checklist for any business to secure its data, users and business operations. This is based on our SAFE (Secure Authenticate Fortify and Enforce) security approach to limit exposure and protect a business and its users. This checklist covers users and organisations that operate WFH, off-site, on-premise, cloud and hybrid models.
So-called ‘bad actors’ or hackers get into a business using three common paths: Your Users, your Network/Infrastructure or Your Applications and/or Data.
Our objectives is to reduce the possibility of being exploited and limit your exposure.
Data Protection:
Security management for your data and infrastructure
Secure Configuration:
Operational hygiene and access management for all services
Roles-Based Access Controls:
Protect data and Applications by using needs-based access
Privileged Access Control Management:
Mange access controls to limit data exfiltration
Securing Users and Data:
Protect users from themselves and ensuring viable data continuity
Networking and Security Services
Responsive, reliable and effective business-oriented servicesNetworking and Security Services
Wide range of managed networking and security services. Browse service offerings for:
End User Computing
Extensive monitoring and Service desk servicesEnd User Computing
Wide range of end user services. Browse offerings for:Managed IT
You name it, we manage ITManaged IT
Deal with the managed IT service experts. Browse service offerings for:Case Studies

PCCS: Enhancing Operational Efficiency and Service Delivery
PCCS Enhancing Operational Efficiency and Service Delivery at Primary & Community Care Services (PCCS) with ‘’mcrIT has been instrumental in transforming our IT infrastructure, allowing us to focus on what we do best - supporting our clients and carers. Their expertise and proactive approach have streamlined our operations, improved our network reliability, and enhanced our overall [...]

Kids’ Cancer Project’s Digital Transformation Case Study
Enhancing Childhood Cancer Support with mcrIT and Microsoft’s Transformational Solutions Digital Transformation Solution ‘’Our partnership with mcrIT has not only streamlined our operations but also reinforced our commitment to our cause. With their unwavering support, we’re better equipped than ever to do our best job in raising funds to support vital kids’ cancer research, all while embracing [...]
Odyssey House Managed Network Case Study
Odyssey House Managed Network Solution ‘’mcrIT have made my job as CEO easier. The staff are happier, the clients are happier, and we have a very reliable system and a great partnership” Julie Babineau, CEO, Odyssey House About Odyssey House Odyssey House is dedicated to the provision of a diverse range of [...]
Why Choose Us
- 100% Australian owned and operated
- Local vendor certified engineers
- 30 years of delivering quality solutions and services in Australia
What Our Clients Say
I recommend mcr to any company that requires a high level of responsiveness, technical proficiency, and a secure IT environment